I. Purpose
This Standard supports and supplements FSU Technology Policies and provides additional security and privacy best practices. It defines the requirements for detecting, analyzing, prioritizing, and handling Information Security Incidents. Security incidents can occur when an FSU student, staff, contractor, or faculty member violates FSU security and privacy policies and standards, specific legal requirements, or contractual obligations. Malicious outside entities may also attempt to comprise systems. A prompt, effective response to a security breach may help minimize loss of information and disruption of services caused by incidents.
Compliance with this Standard is mandatory and is enforced in the same manner as the policies it supports. Standards will be periodically reviewed and updated as necessary to meet emerging threats, changes in legal and regulatory requirements, and technological advances. All users are required to comply with FSU policies or obtain an exception in accordance with the 4-OP-H-25.20 Request for Exception to IT Security Policy.
II. Definitions
Consolidated University Unit – a consolidated group of related university units that has management authority and responsibility for compliance with IT policies, standards, and guidelines.
Incident Response (IR) Plan – documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of malicious cyberattacks against an organization's information system(s).
Information Security Incident – a suspected, attempted, successful, or imminent threat of unauthorized access, use, disclosure, breach, modification, or destruction of information; interference with information technology operations; or significant violation of responsible use policy.
IT Assets - technology resources including, but not limited to, computers, networks, servers, applications, databases, software, and operating systems that are owned by, managed by and/or sponsored by IT Asset Custodians.
Full IT Glossary
III. Standard
FSU has adopted the NIST Cybersecurity Framework (CSF) 2.0 as the foundation for a risk-based approach to cybersecurity management. CSF uses common cybersecurity functions, activities, and desired outcomes to align university policy to the management of IT risk. The CSF Core leverages industry standards, guidelines, and best practices to establish baseline expectations for cybersecurity for all University Units.
University Units are responsible for using this framework to assess their unique risks, threats, vulnerabilities, and risk tolerances to determine an appropriate risk management plan that complies with FSU Technology Policies, Standards and Guidelines.
Functions supporting this Standard include, but are not limited to:
NIST Cybersecurity Framework 2.0
| Function | Category |
| Identify (ID) |
Improvement (ID.IM): Improvements to organizational cybersecurity risk management processes, procedures and activities are identified across all CSF Functions. |
| Detect (DE) | Anomalies and Events (DE.AE): Anomalous activity is detected and the potential impact of events is understood. |
| Respond (RS) | Incident Management (RS.MA): Responses to detected cybersecurity incidents are managed |
| Incident Mitigation (RS.MI): Activities are performed to prevent expansion of an event and mitigate its effects | |
| Incident Response Reporting and Communication (RS.CO): Response activities are coordinated with internal and external stakeholders as required by laws, regulations, or policies | |
| Recover (RC) | Incident Recovery Communication (RC.CO): Restoration activities are coordinated with internal and external parties |
Full CSF Crosswalk to Controls: NIST Crosswalk
*The above NIST chart describing Cybersecurity Framework and Controls and the link to other NIST Crosswalk principles and information in no way belongs to or is owned by Florida State University.
For more information on Security incident response best practices, see SP 800-61 Rev. 3, Incident Response Recommendations and Considerations for Cybersecurity Risk Management: A CSF 2.0 Community Profile | CSRC.
Roles and Responsibilities
Chief Information Security Officer (CISO) and Information Security and Privacy Office (ISPO)
The CISO directs the Information Security and Privacy Office (ISPO) for the university. The CISO reports to the FSU Chief Information Officer and the Provost and also serves as the Chief Privacy Officer for FSU. The CISO and ISPO are responsible for establishing and enforcing the application of appropriate operational security controls necessary to protect the network.
Consolidated University Unit (CUU) Dean, Director, or Department Head (DDDH)
The Dean, Director, Department Head, or other managerial position responsible for protecting the confidentiality, availability, and integrity of university IT Assets within a CUU. The CUU DDDH has responsibility for ensuring IT security and privacy for the units within the CUU.
Consolidated University Unit (CUU) Information Security Manager (ISM)
The liaison designated by the CUU Dean, Director, or Department Head (DDDH) responsible for coordinating the CUU’s information security program. The CUU ISM is the central point of contact between the University Units and ISPO for security issues. CUU ISM responsibilities will be included in position descriptions.
University Unit Information Security Manager (ISM)
The liaison designated by a University Unit Dean, Director, or Department Head (DDDH) responsible for ensuring a university unit’s compliance with security IT policies, standards, and guidelines, in coordination with their designated CUU’s information security program.
IT Asset Custodian
An individual with responsibility for the configuration, implementation, management, monitoring, oversight, and day-to-day operations of university IT Assets. IT Assets include but are not limited to enterprise or distributed networks, computers. servers, workstations, IoT devices, applications, databases, operating systems, and firmware.
For more information, see IT Roles and Responsibilities.
Security Incident Response Planning
Security incidents occur when an FSU student, staff, contractor, or faculty member violates FSU IT Policies and Standards, specific legal requirements, or contractual obligations. External entities may also target IT resources resulting in security incidents.
University Unit ISMs and CUU ISMs are responsible for ensuring appropriate Incident Response management and compliance for all IT Assets for the units within the CUU:
- IT Asset Custodians are responsible for providing incident response information for IT Assets they manage.
- University Unit ISMs are responsible for developing and maintaining an Incident Response (IR) Plan for the University Unit’s IT Assets.
- University Unit IR Plans shall be made available to the CUU ISM. CUU ISMs are responsible for aggregating the University Unit Plans as needed to ensure a quick and coordinated response to incidents and dissemination of information to IR participants.
- Response team members must be identified and provided regularly scheduled training to effectively manage incident response activities.
- IR Plans must be reviewed and tested annually, or sooner if significant changes occur which could impact the plan. Results of IR Plan testing, including lessons learned, must be documented and incorporated into the plan to address weaknesses and additional incident scenarios needed.
- IR Plans shall be made available to ISPO upon request.
Security Incident Response Steps
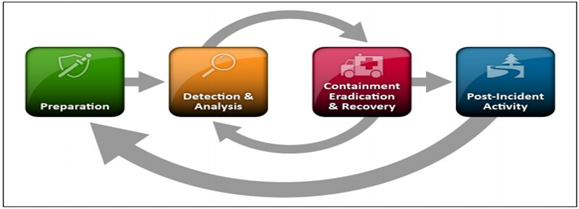
NIST Incident Response Life Cycle
IR Plans shall address the following phases of the Incident Response Life Cycle, commensurate with the value of the IT Asset and the level of risk:
- Preparation
IT Asset Inventory - Inventory IT Assets, including but not limited to servers, networks, applications, and critical devices. Rank IT Assets by level of importance and risk to determine the level of appropriate response required for incidents. Risk level is determined by the IT Asset Custodian based on factors including, but not limited to:
- the sensitivity and risk of harm to individuals or FSU if the IT Asset or High Risk/Moderate Risk data is subject to a breach or unauthorized disclosure. (For more information see 4-OP-H-25.01 Data Security Standard.)
- failure or loss of availability of a critical business function.
- loss of productivity or other negative impacts to resources.
Communication – Develop a communication plan including contact information for the primary and backup individuals responsible for managing the incident; internal, management or third-party personnel; and any others involved or required to be notified as defined by this Standard. Information to be reported includes contact information (names, phone numbers, email addresses, secure method of communication, and verification of identity instructions), timeframes, mechanisms for reporting and any other reporting requirements based on the type of incident. Identify security incident thresholds that would require investigation. Develop a process and baseline IR Plan for each type of incident to be used if needed.
All dissemination of information to the media related to university IT security events will be managed by University Communications. Refer all information requests to that office.
- Detection and Analysis
In addition to anticipated risks, focus on preparations to handle incidents that use common attack vectors (external/removable media, web, email attachments, theft of equipment, etc.). Information related to the incident must be gathered and appropriate research performed to determine the entry point, extent of the breach and any additional notifications required.
Reporting requirements must be documented and may vary depending on the type of security incident and risk level.
- Containment, Eradication and Recovery
Containment is intended to quickly patch the entry point of a threat before resources are overwhelmed or damaged. Containment strategies vary based on the type of incident, so each type of incident should have a containment strategy. Containment examples include system shut down, disconnection from the network or disabled functions.
Eradication may be necessary after containment to eliminate the threat. If so, all affected hosts affected within the infrastructure must be identified and remediated. Eradication examples include deletion of malware, disabled breached user accounts and mitigation of vulnerabilities that were exploited.
Recovery includes restoring systems to normal operations, confirming functionality and remediating vulnerabilities to prevent similar incidents. Recover examples include restoring systems from backups, rebuilding systems from scratch, installing patches and changing passwords.
- Post-Incident Activity
This step focuses on follow-up, lessons learned, coordination and information sharing, and process improvements to reduce the likelihood of recurrence of similar incidents. Lessons learned should be used to update IR Plans.
For more information, see the SP 800-61 Rev. 3, Incident Response Recommendations and Considerations for Cybersecurity Risk Management: A CSF 2.0 Community Profile | CSRC.
Reporting Of Security Incidents
All Users
Users are required to immediately report suspected or confirmed Information Security Incidents, as defined by this standard, to the Chief Information Security Officer (CISO) at security@fsu.edu.
Users are responsible for safeguarding security tokens, smart cards, identification badges, or other devices used for authentication and access to secured IT facilities. It is the responsibility of each FSU student, staff, contractor, or faculty member to immediately report the loss or suspected loss of any of these devices providing secured access to the appropriate unit or facility coordinator, and the University Unit ISM.
University Unit ISMs
University Unit ISMs are responsible for reporting all confirmed or suspected Information Security and Privacy Incidents to the CUU ISM and the Chief Information Security Officer (CISO) at security@fsu.edu.
IT Asset Custodians
IT Asset Custodians are responsible for notifying the University Unit ISM and the CUU ISM of any security incidents, as defined by their IR Plan for the IT Asset.
University Unit ISMs and CUU ISMs
The University Unit ISM in conjunction with their CUU ISM, is responsible for coordinating and reporting suspected or confirmed security and privacy incidents with the appropriate entities, including but not limited to:
- The CISO/ISPO will be notified immediately of all security incidents that are threatening other IT resources (e.g. hacking of a mail or webserver, etc.).
- FSU Police Department (FSU PD) will be notified of criminal activity and incidents such as threats to human beings or property, harassment or other criminal offenses involving user accounts, credit card fraud, child pornography, loss or theft of computing devices, breaches of Criminal Justice Information Services (CJIS) information and compromise of High Risk or Moderate Risk data. FSU PD will serve as liaison with other law enforcement entities (FBI, FDLE, other federal, state, and local) as needed.
- The University Unit DDDH and CUU DDDH will be notified for security incidents involving payment card data breaches, suspected or actual incidents involving CUU IT Assets and critical systems, and compromise of High Risk or Moderate Risk data.
- Incidents involving misuse of FSU IT resources by employees, employee misconduct (criminal or otherwise), and violations of the 4-OP-H-21 Acceptable Use of Technology Policy must be reported to the Office of Human Resources.
- Incidents involving misuse of FSU IT resources by students must be reported to the Office of Student Rights and Responsibilities.
- Incidents of a technical nature, including unauthorized computer access; compromise of Personally Identifiable Information (PII) or other Federal regulations (FERPA, HIPAA, GLB) and contractual obligations (PCI DSS); root attacks on critical IT Assets or the infrastructure; Denial of Service attacks that impair the availability of FSU computing resources; malicious code attach/malware; compromise of user logon account credentials; etc. must be reported to the CISO at abuse@fsu.edu immediately upon discovery.
- Suspected fraud activities may also be reported to the FSU Ethics Point hotline at
855-231-7511
See Information Technology Security and Privacy Incident Response and Reporting Procedures for additional information.
IV. Resources
CIS Tabletop Exercises
Sample tabletop exercises provide cybersecurity scenarios that can be used as a learning opportunity by CUUs in developing Incident Response Plans.
CRR Supplemental Resource Guide, Vol 5 Incident Management
This document provides information and sample templates for Risk Management and Incident Response planning.
CIS Control 17: Incident Response Management Controls Assessment
This document contains information about Incident Response
